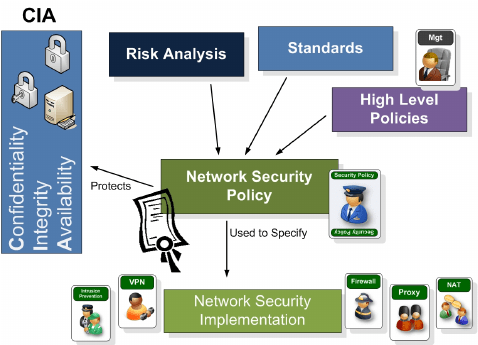
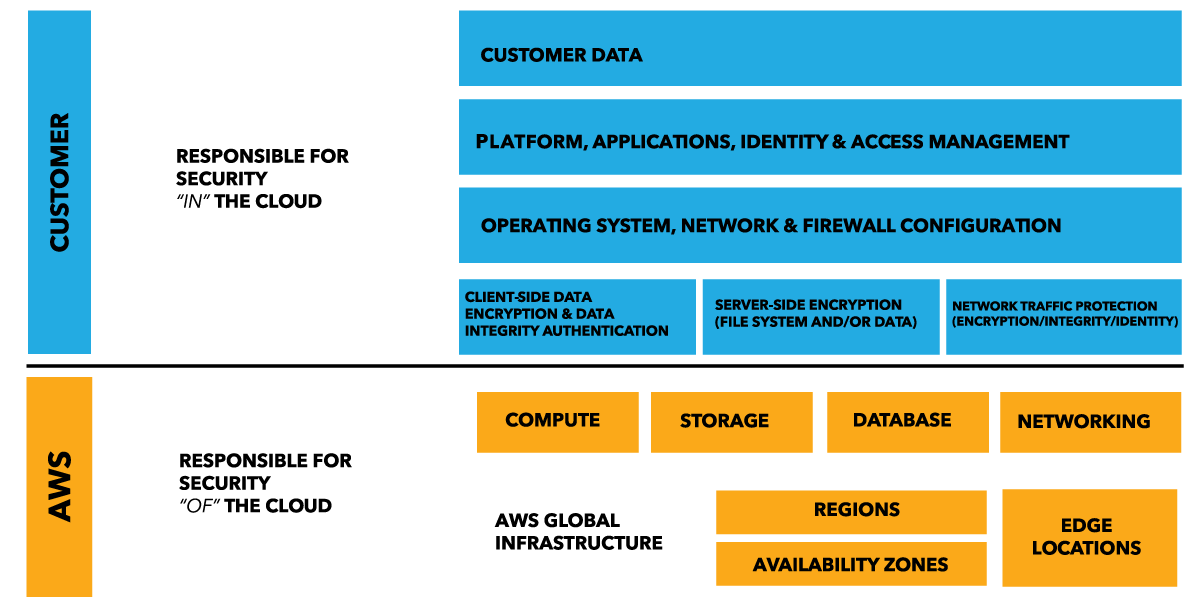
According to a study published in the Harvard Corporate Review, the cloud’s most significant advantage is its ability to speed up business processes. Business agility is an essential component in cloud adoption, as seen by 32% of respondents who cite this as their primary reason for using the cloud. Creative output went up by 14 percent, while costs went down by 13 percent due to the program.
In a study by McKinsey & Company, they found that agility may lead to faster revenue growth, more significant and more lasting cost reduction, and better management of risks and reputational problems, all of which are positives. To succeed in today’s highly competitive business world, a company must be flexible. If you employ cloud computing services, you may increase your company’s agility.
Business agility refers to a company’s ability to swiftly and cost-effectively adapt to changes in the business environment. Adaptability is a critical component of corporate agility. Adaptability, coordination, and flexibility are all under the umbrella of agility.
Agility in Cloud Computing
In today’s challenging business environment, enterprises can no longer depend on their present business and IT strategies. Nowadays, modernization is a faster process than a decade ago, thanks to social, mobile, analytics, and cloud computing. The cloud makes it simpler to optimize existing IT systems to increase operational efficiency and promote organizational agility and growth.
Skilled cloud analysts and consultants, software developers, and DevOps engineers work together at EES to deliver best-in-class cloud computing consulting services. With us, you reward your business with a resilient and top-performing cloud with no downtime.
As business habits change, you can take advantage of this opportunity. In an agile environment, new business processes may be implemented, or existing ones can be adapted. This change in practices necessitates changes or additions to IT resources. Companies may quickly and easily add or adjust IT resources to adapt to their changing business needs thanks to cloud computing services.
Development and testing staff may be summoned on demand. Resources are needed for the testing and development of software. Commercial opportunities may be delayed by the time it takes to acquire additional resources and integrate them into the existing infrastructure. This might be a business risk because of the expenditure of money on new and expensive resources. A cloud-based design reduces the need for on-demand access to resources to address these problems, which saves time. The initial expenses involved with acquiring new hardware and software are eliminated by using cloud-based payment systems.
The pay-per-resource approach to project implementation and testing saves money by reducing the number of new resources purchased and made available. IT capital expenditure is no longer required in the company’s overall budget. Cloud-based models make it possible to handle an unanticipated IT cost with no effort.
To speed up your company’s operations and transactions, the cloud is the answer. Cloud-based applications allow enterprises to access their components and engage more effectively with customers over the internet. With more significant time and resources available, IT teams can spend more time creating and deploying innovative applications that directly influence the organization’s bottom line.
Cloud computing significantly reduces the time it takes to provide IT infrastructure, resulting in speedier delivery of IT projects critical to revenue growth or cost reduction. A cloud server may be up and running in a matter of minutes, but a physical server might take days or weeks to set up.
With cloud computing, resource deployment and de-deployment may be automated. Cloud computing reduces the time spent by IT systems administrators because of its efficiency.
Businesses may reap the benefits of cloud computing by simply paying for the services they use. Cloud computing’s pay-as-you-go concept allows users to rent or subscribe to different infrastructure components, software systems, and data services as required. Such resources like storage space for the entities themselves may not be worth the money spent on their acquisition.
Cloud computing can improve product development and marketing campaigns that better align IT expenditures with the business’s goals. Change is no longer seen as an impediment but as an opportunity because of the cloud’s scalability. An organization’s activities can be stepped up or toned down to fulfill its business goals, such as the acquisition and retention of new customers and a rapid pace for the launch of new products.
You no longer have to wait for hardware or software since everything is accessible online. Typical corporate methods might take weeks or even months to set up and develop software and hardware. Instead, a cloud-based version of the same setup may be ready in only a few hours.
The cloud’s pay-as-you-go flexibility and quick expansion in response to changing business demands help end-users. Regular workloads like testing and development, load testing, seasonal traffic spikes, a new application, and others need on-demand scalability.