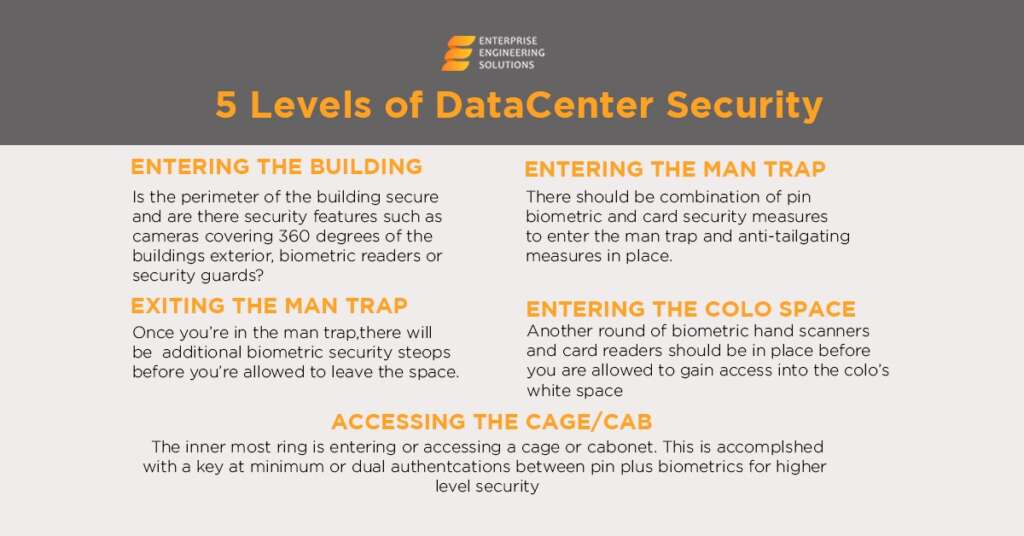
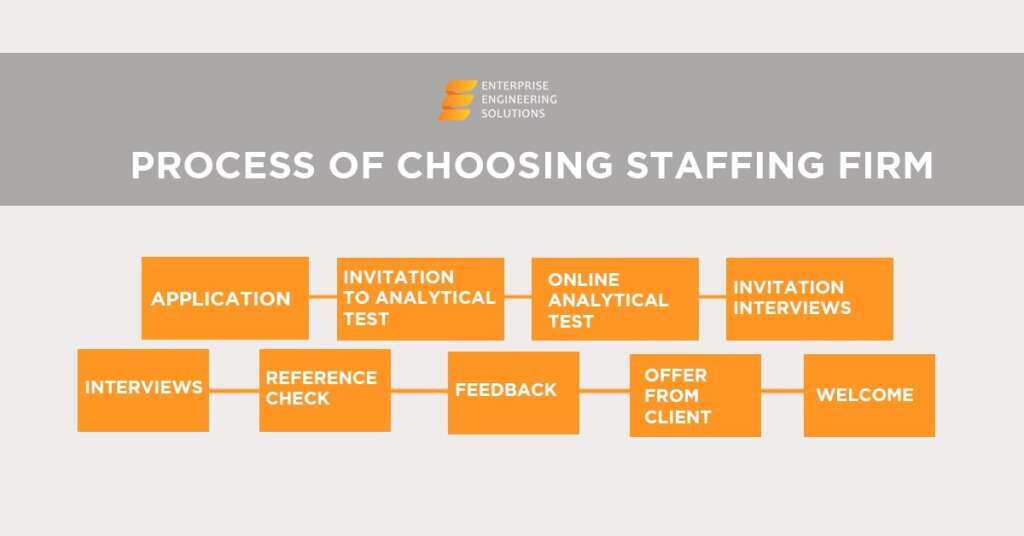
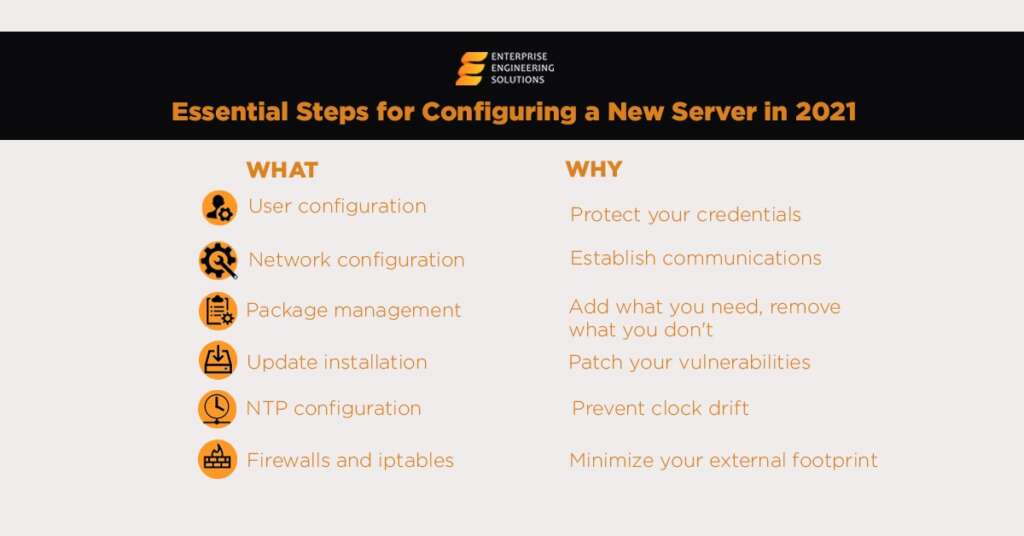
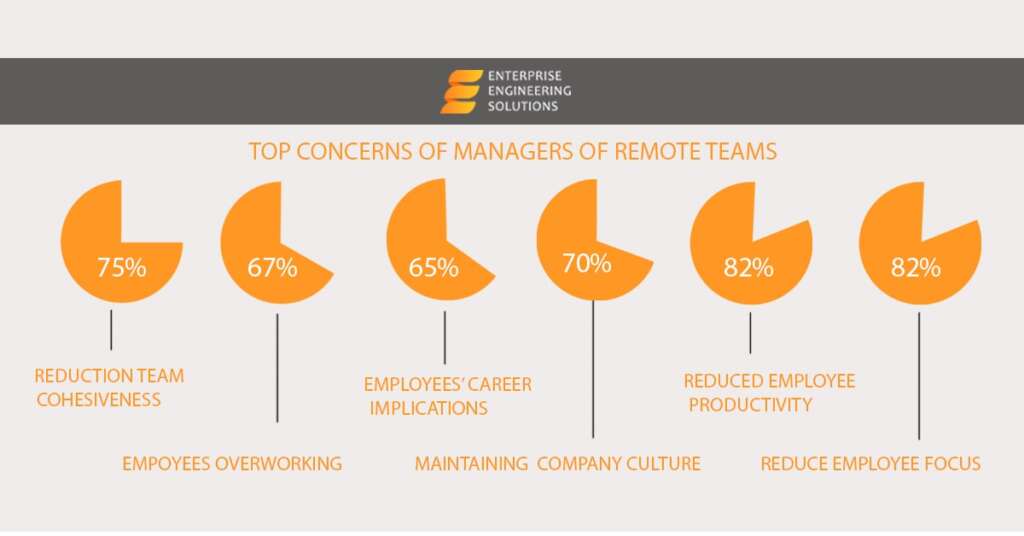
Machine learning is part of artificial intelligence. It is used in technology, business industries, and processes that need automation. Furthermore, machine learning lets you work on hundreds and thousands of screens simultaneously without hassle.
Machine Learning is the study of how machines are made more humane in their performance and judgments, enabling them to learn and design their programs. The learning process is automated and enhanced based on machine experiences throughout the procedure. EES’s machine learning consulting services include plenty of solutions including, data mining, robotic process automation, computer, and 3D vision, deep and reinforcement learning, natural language processing, and so many more. All ML-related services are based on emerging technologies.
Good quality data is also supplied to the machines, and various methods are employed to create ML models to train machines. The algorithm selection depends on the type of data and the type of activity to automate.
Nowadays, Machine Learning has all the features it needs or users demand. Machine learning can automate many jobs, particularly those which only humans can carry out with their natural intellect. Duplicating this intelligence on machines acquired by machine learning is marvelous.
Machine learning work in a different way. It helps in the data gathering. It completes the learning process by using specified machine inputs. Such programs make machines operate hassle-free. Machine learning can understand or automate decision-making when people cannot understand.
What Are the Valuable Uses of Machine Learning in the Recruitment Process?
Machine learning automatically works in different techniques now. ML spends a lot of time redefining the recruitment processes. It is supposed to speed up manual operations that waste more than enough time for recruiters and managers—for example, going through thousands of applications. Technology allows people more time to carry out more valuable jobs.

To help you understand how artificial intelligence for recruitment adds into your stuff:
Assessment Strategy
Machine learning can be used to build an assessment approach. Hiring and recruitment managers can store the assessment metrics in their machine study model for once. Finally, they can track how they do and assess your defined factors. We can quickly evaluate the progress of the candidate automatically through reliable machinery. It is successfully creating a revolutionary flair in the current recruitment environment. For instance, machines can read your candidate’s attempted tests, machines can comprehend their feelings, etc.
High-level of Accuracy
The recruiting of machinery uses objective data. Therefore the chances of flaws and human errs are entirely excluded from the recruitment process. No more judgmental human mistakes! Machine learning has so many advantages over the traditional recruitment procedure. It is, therefore, right to recommend the use of machine learning as it transforms the whole recruitment process.
Testing of CVs Screening
CV screening is another time-demanding process for hiring and recruitment. Many machine learning-powered screening technologies are meant to address this challenge. Such technologies examine CVs and recognize keywords that match the characters, talents, and work experience. It saves your time and effort. It definitely promotes the implication of machine learning in the recruitment process.
Search Procedure
If you certainly want the best candidate, you must not rule out searches for such persons. That can deny you of recruiting the most acceptable individual. Machine learning can help find candidates for the standard procurement methods, recruitment, and screening. Based on all these factors, machine learning is an excellent recruitment tool. It can cover all holes in the recruitment process and focus on a human element.
The best thing is that the recruiting agency for machine learning is developing at an astonishing pace and can accelerate the recruitment process and produce more relevant results.
Suggestions Become Easier
One of the biggest advantageous roles of machine learning in the recruitment process. Many employment managers utilize various recruitment sites to find able employees and limit their qualified candidates’ lists. They select candidates based on characteristics, skill, business, and know-how. Recruiters do not have to feed every detail and dig from hundreds of applications. They can only depend on employment portals and networking sites to use machine learning and provide suggestions to candidates who best suit the role.
Bias Exclusion
Another technique to develop recruitment that can help machine learning is to provide equal coverage to all chances, whatever of the candidate’s history. Its algorithms are centered on skills and do not concentrate on the university of the applicant or past firms, or sex or race.
Conclusion
The number of data available to companies is massive. That is why we need the extra speed to cope with the upcoming information. Machines use this data to learn better approaches to enhance the outcomes. These results can be beneficial for providing valuable visions and knowledgeable business decision-making. Machine learning is constantly increasing, increasing its application in personal and professional lives. We make greater use of machine learning than we know it in our daily lives.
In the future, machine learning will only grow and serve us. Now, you know brilliantly Machine Learning In Recruitment Process simplifies the whole procedure. Undoubtedly, machine learning is a modern invention for us. Through machine learning, we can conduct the hiring and recruitment process quickly.